For enabling wired MAC bypass on Cisco switches there are two commands available.
- dot1x mac-auth-bypass — the Access-Request message is a Password Authentication Protocol (PAP) authentication request
- dot1x mac-auth-bypass eap — the Cisco switch perform MAB as EAP-MD5 authentication
Although PAP authentication has been configured by the switch as well as authentication method in Microsoft NPS Server, authentication does not work. The NPS logs showing rejects for the reason of a not configured protocol type; EAP with type MD5. Sniffing with Network Monitor confirmed Cisco requests EAP communication.
Some researches brought me to the following statement:
In this release, the RADIUS security system with Extensible Authentication Protocol (EAP) extensions is the only supported authentication server.
In current NPS implementation EAP-MD5 cannot be chosen for authentication.
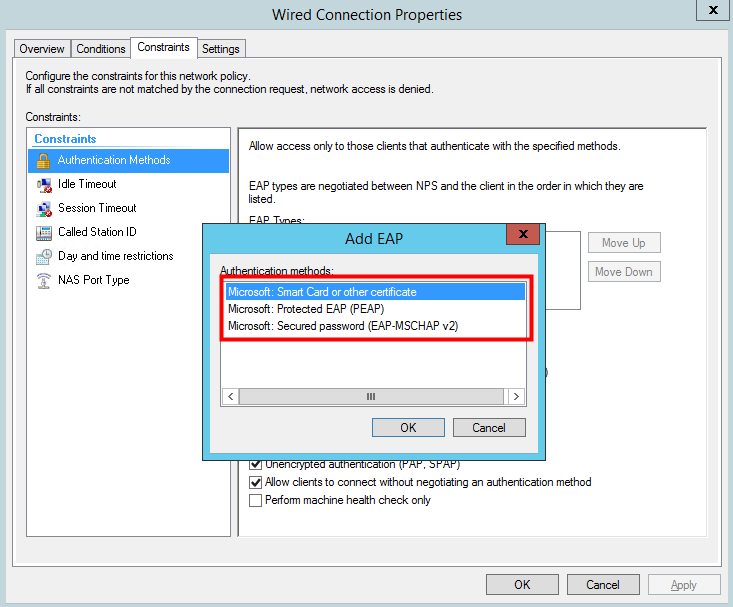
MD5 Challenge is being deprecated and no longer supported since Windows Server 2008/Vista. It can be re-enabled by modifying the registry on the NPS Server, but without any support!
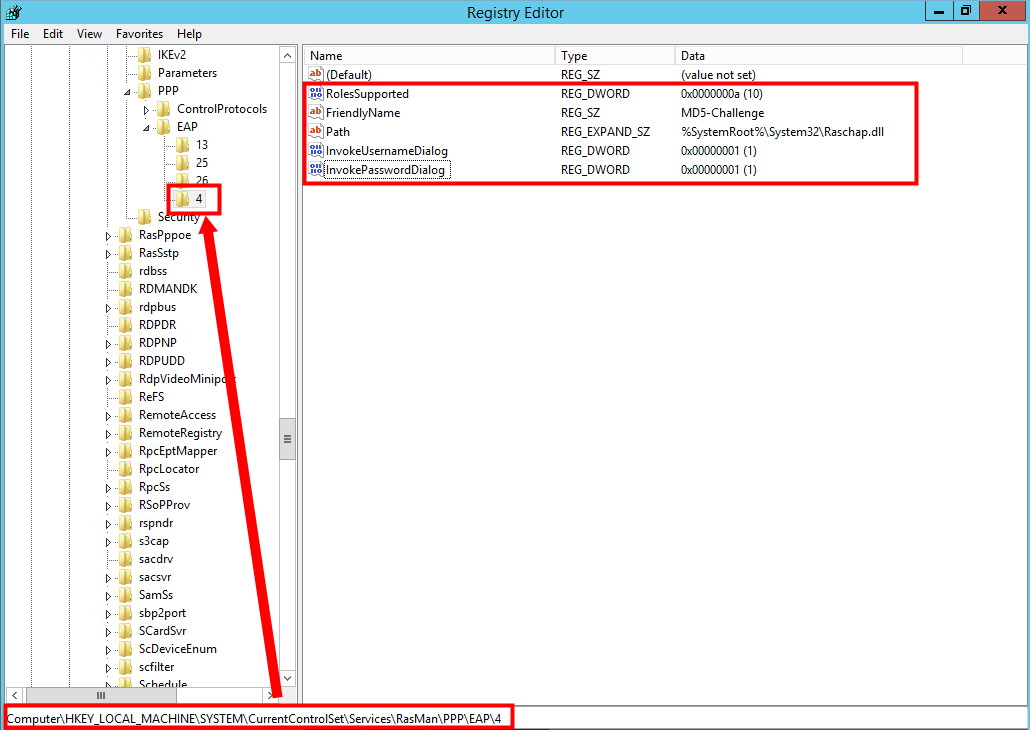
registry import
|
1
2
3
4
5
6
7
8
9
10
11
12
|
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RasMan\PPP\EAP\4]
"RolesSupported"=dword:0000000a
"FriendlyName"="MD5-Challenge"
"Path"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,52,00,\
61,00,73,00,63,00,68,00,61,00,70,00,2e,00,64,00,6c,00,6c,00,00,00
"InvokeUsernameDialog"=dword:00000001
"InvokePasswordDialog"=dword:00000001
|
when values are set, restart the NPS Service
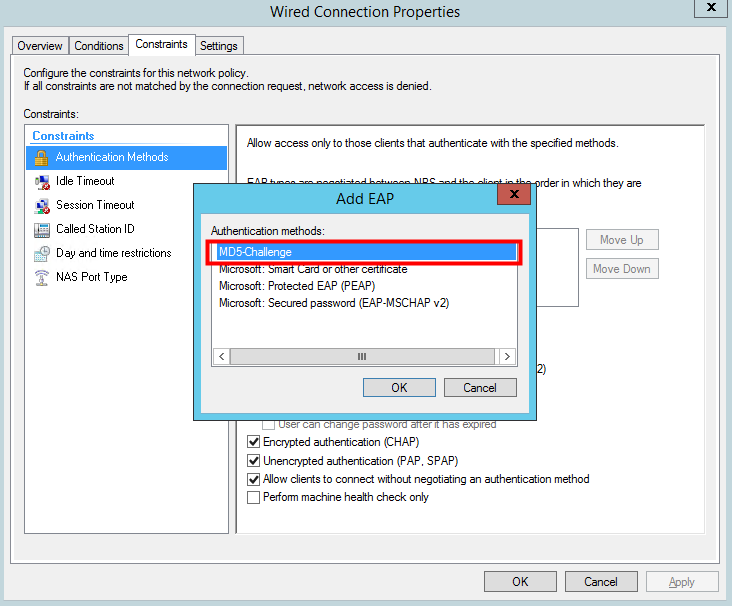
NPS log
Log Name: Security
Source: Microsoft-Windows-Security-Auditing
Event ID: 6278
Task Category: Network Policy Server
Level: Information
Keywords: Audit Success
User: N/A
Network Policy Server granted full access to a user because the host met the defined health policy.
Authentication Details:
Authentication Type: EAP
EAP Type: MD5-Challenge
Windows Server 2012R2